Using Azure Security Score
First version: 2023-01-27
Last updated: 2024-03-21
Last update(s): Some more detailed explanations. Will be adding more recommendations over time.

The Azure Security Score is a valuable tool to identify, understand and improve the security posture with respect to Azure resources. anDREa recommends the local Research Support Team to check and possibly improve the Azure Security Score once a month. If you're a Research Support Team member and want to know more, you can schedule an appointment with anDREa's Security Officer.
The Azure Security Score is based on a combination of factors such as network security, identity and access management, and data protection. By identifying and addressing these issues, you can improve the security posture and reduce the risk of a security incident.
However, be aware that this is a score of what Azure thinks is secure. Please take in account your own organization's security demands. And, not all flagged items can resolved.
This article describes how to use Azure Security Score using a Subscription. The principle is the same if you do it on another level like a Resource Group which equates to a Workspace in the myDRE setting.
There are two main sections (use the TOC to navigate quickly):
- Azure Security Recommendations
- Azure Security incidents and alerts
Azure Security Recommendations
- Log in to the portal.azure.com with your ST account
- Go to Subscriptions
- Select a subscription belonging to your organization.
- On the left hand side, click on Security
- Recommendations - use the explanation below
Recommendations explained
Machines should have a vulnerability assessment
Type | REMEDIATE |
Who | Any member of the Workspace, optionally Researcg Support Team (if added to the Workspace as a member). |
Option 1 | Start VM, install the vulnerability assessment solution and other updates. This mostly pops up when updates are available within the VM or if outdated software is being used within the VM.
The anDREa team is working on an Update Management Center to make this more insightful for the user.
|
Option 2 | Delete the VM if it is no longer used. |
Objective | Once this is done, this recommendation should disappear. |
Install endpoint protection on virtual machines
Type | REMEDIATE |
Who | Any member of the Workspace, optionally Research Support Team. |
Option 1 | Start VM, install the vulnerability assessment solution and other updates. |
Option 2 | Delete the VM if it is no longer used. |
Objective | Once this is done, this recommendation should disappear. |
Log analytics agent should be installed on virtual machines
Type | REMEDIATE |
Who | Any member of the Workspace, optionally Research Support Team. |
Option 1 | Start VM, install the vulnerability assessment solution and other updates. This mostly pops up when updates are available within the VM or if outdated software is being used within the VM.
The anDREa team is working on an Update Management Center to make this more insightful for the user. |
Option 2 | Delete the VM if it is no longer used. |
Objective | Once this is done, this recommendation should disappear. |
Machines should have vulnerability findings resolved
Type | REMEDIATE |
Who | Reseach Support Team, optionally anDREa Support Team. |
Option 1 | A Monitoring Agent needs to be installed on the VM using a script. |
Objective | Once this is done, this recommendation should disappear. |
Storage accounts should restrict network access using virtual network rules
Type | VERIFY / REMEDIATE |
Who | Support Team |
Assess | Assess whether the storage accounts listed here are not Workspace storage accounts. |
Action 1 | It is acceptable if only diagnostic and cloud shell storage accounts show up. |
Action 2 | If there are Workspace storage accounts listed, then this is a high risk/red flag. Contact anDREa. |
Objective | Accept if it is expected, remediate through anDREa when it is unexpected. |
Adaptive network hardening recommendations should be applied on internet facing virtual machines
Type | VERIFY |
Who | Research Support Team |
Assess | Assess the listed Workspaces. These are most likely Workspaces with a lot of network rules enabled or full internet access enabled. |
Action 1 | Disable full internet access. |
Action 2 | Contact users to disable network rules or full internet access. |
Objective | Accept if it is expected or resolved. |
A maximum of 3 owners should be designated for subscriptions
Type | VERIFY |
Who | Research Support Team |
Assess | Assess who is Subscription Owner by inheritance. |
Action | If Subscription Owners show up that you do not recognize or should not be owner, contact anDREa. |
Objective | Accept if it is expected, remediate through anDREa when it is unexpected. |
There should be more than one owner assigned to subscriptions
Type | VERIFY |
Who | Research Support Team |
Assess | Assess who is Subscription Owner by inheritance. |
Action | Contact anDREa if there are NO owners, one is fine. More is also fine. |
Objective | Accept if it is expected, remediate through anDREa when it is unexpected. |
Keyvaults should have purge protection enabled
Type | WORKED UPON |
Who | anDREa |
Objective | Accept, after work completion the recommendation will disappear. |
Deprecated accounts with owner permissions should be removed from subscriptions
Type | VERIFY |
Who | Research Support Team, request for anDREa Support Team to remove Subscription Owners which do no longer work at the organisation. |
Objective | Accept. |
Deprecated accounts should be removed from subscriptions
Type | WORKED UPON |
Who | anDREa, Support team after work completion. |
Objective | Accept, after work completion the recommendation will disappear. |
Diagnostic logs in Key Vault should be enabled
Type | WORKED UPON |
Who | anDREa |
Objective | Accept, after work completion the recommendation will disappear. |
Storage accounts should use a private link connection
Type | ACCEPT |
Explanation | Private link connections do make a Workspace a lot more secure, but these are quite expensive and are not needed for a standard Workspaces. |
Alternative | If needed, contact anDREa. |
Type | ACCEPT |
Explanation | Private link connections do make a Workspace a lot more secure, but these are quite expensive and are not needed for a standard Workspaces. |
Alternative | If needed, contact anDREa. |
Management ports of virtual machines should be protected with just-in-time network access control
Type | ACCEPT |
Explanation | The recommendation itself is important, however anDREa uses its own implementation of just-in-time network access control. Therefore, this recommendation will show up in every subscription. |
Objective | Accept, this recommendation is expected to show up in every subscription.
|
Guest configuration extension should be installed on machines
Type | ACCEPT |
Explanation | anDREa does not do configuration management on VMs, so this is expected to be flagged in every subscription. |
Objective | Accept, this recommendation is expected show up in every subscription. |
Firewall should be enabled on Keyvault
Type | ACCEPT |
Explanation | This recommendation cannot be achieved in the current state. anDREa will keep an eye on updates. Keyvaults can however only be queried by Workspace Accountables/Privileged members. |
Objective | Accept, this recommendation will show up in every subscription. Will be worked on once updates are available. |
Azure Backup should be enabled for virtual machines
Type | ACCEPT |
Explanation | anDREa does not enable Azure Backup by default, this is quite expensive. Moreover, Virtual Machines are viewed as disposables, it is easy to set up a new Virtual Machine. |
Objective | Accept. If Azure Backup is really needed, it can be requested. Contact anDREa. |
Subnets should be associated with a network security group
Type | ACCEPT |
Explanation | Per Subscription, 100 subnets are available for Workspaces. If there are 10 Workspaces created, it means that at least 90 subnets are not associated with a network security group. Once a Workspace is created, subnet will be associated with a network security group. Therefore, this recommendation can be ignored. |
Objective | Accept. |
Storage account public access should be disallowed
Type | ACCEPT |
Explanation | This recommendation can be ignored and this is expected to show up in all subscriptions. The storage account settings are set to ‘only accessible to virtual networks and IP addresses’. Azure flags this as public, but in fact it is not publicly accessible. It is only accessible from within the associated Workspace. |
Objective | Accept, this recommendation is expected to show up in every subscription. |
Two recommendations to verify if the VM and data is encrypted
In the same screen, click on View additional recommendations on Defender for Cloud.
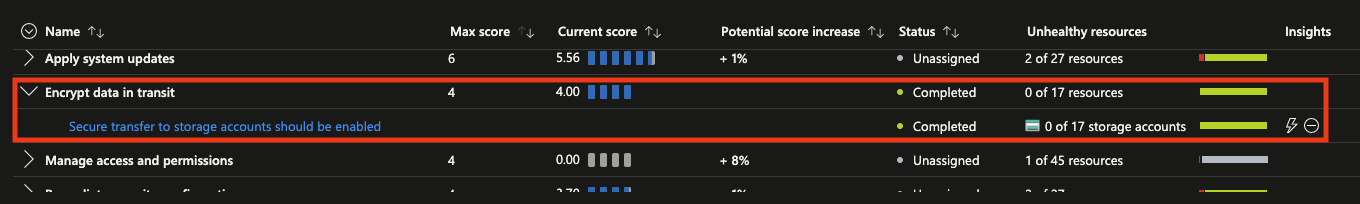
- The status should be on Completed and there should be 0 unhealthy resources.
- If this deviates, please contact anDREa to remediate.
Security incidents and alerts
- Log in to the portal.azure.com with your ST account
- Go to Subscriptions
- Select a subscription belonging to your organization.
- On the left hand side, click on Security
- Security incidents and alerts - use the following steps
- Click on the alert
- Click on the alert once more
- Click on View full details
- Investigate the alert details
Under related entities, you can unfold the Account pane and find the AAD User ID.
- Assess based on Alerts Explained section
Alerts explained
Unusual execution of custom script extension in your virtual machine
Type | VERIFY |
Who | Research Support Team |
Explanation | This alert is seen in several subscriptions. Usually it is because a VM was removed and then a new one added. To able to log into a VM, a script adds the -RdpUsers group. This can be flagged as unusual execution of custom script extension. |
Action 1 | Click on the alert twice and click on View full details. Under the Account pane you should be able to find the AAD User ID. Activate your User Administrator PIM role and copy paste the AAD User ID in the search bar of the AAD.
Check all of them to see if it is a known entity:
- digital research environment app (weu-andrea)
- licenseadmin
|
Objective | Accept if it is expected, remediate through anDREa when it is unexpected.
|
Traffic detected from IP addresses recommended for blocking.
Type | VERIFY |
Who | Research Support Team |
Explanation | This alert is popping up from time to time in specific Client subscriptions, most likely because they mask their on-premise IP addresses. This is also expected to show up in the Shared Subscription if you're making a template for the whole organisation. |
Action 1 | Check the details of the alert. |
Objective | Accept if it is expected, remediate through anDREa when it is unexpected. |
Unusual user password reset in your virtual machine
Type | VERIFY |
Who | Research Support Team |
Explanation | This alert has been observed in a test Workspace to solve testing a VM domain joining issueThis alert is expected to be flagged in that specific subscription. It should not appear in other Subscriptions. |
Action 1 | Contact anDREa if it appears in other Subscriptions. |
Objective | Should not occure |
Access from an unusual location to a storage file share
Type | VERIFY |
Who | Research Support Team |
Explanation | This appears also when an IP address is added to a storage account. Changes like this should be documented in a ticket. |
Action 1 | Search for the ticket. If it cannot be verified, please contact anDREa via security-related incidents. |
Objective | Should not occur without a ticket to back it up. |
Access from an unusual location to a storage file share
Type | VERIFY |
Who | Research Support Team |
Explanation | This alert might be for an authorised download. |
Action 1 | Verify with the users that this is indeed an authorised action, if this is cannot be corroborated, please contact anDREa via security-related incidents. |
Objective | Should not occur without unauthorized downloads. |
Related Articles
20230503 - Security Management Report
anDREa's Security Officer annually provides the management board with the Security Management Report. An annual security management report is a key part of this auditing process. The report provides a summary of the organization's ISMS activities, ...
20230503 - Management Response on Security Management Report
anDREa's Security Officer annually provides the management board with the Security Management Report. An annual security management report is a key part of this auditing process. The report provides a summary of the organization's ISMS activities, ...
20220713 Report Azure White Box Security Audit
Version: 2022-07-14 Introduction anDREa has a Pentest Program program as part of the commitment to protect the security of its business information. At least once a year we request an external party to do the pentest and a white box security audit. ...
20220607 Security Management Report
As part of anDREa's commitment to maintaining an Information Security Management System (ISMS) based on ISO 27001 please feel free to download and read the attached anDRE's 20220607 Security Management Report.
20210224 Pentest 2021-Q1 Report & 20210301 White Box Security Audit 2021-Q1 Report
In accordance with our Pentest Program, anDREa engaged nSEC/Resilience for the anDREa White Box Security and the Pentesting 2021-Q1. The core questions being: Can non-authorized people or services access Workspaces or affect anDREa’s core services? ...
